Model Solutions
Introduction
Windows
Firewall with Advanced Security combines a host firewall and Internet Protocol
security (IPsec). Unlike a perimeter firewall, Windows Firewall with Advanced Security
runs on each computer running this version of Windows and provides local
protection from network attacks that might pass through your perimeter network
or originate inside your organization. It also provides computer-to-computer
connection security by allowing you to require authentication and data
protection for communications.
Windows
Firewall with Advanced Security is designed for use by IT administrators who
need to manage network security in an enterprise environment. It is not
intended for use in home networks. Home users should consider using the Windows
Firewall program available in Control Panel instead.
Windows
Firewall with Advanced Security is a stateful firewall that inspects and
filters all packets for IP version 4 (IPv4) and IP version 6 (IPv6) traffic. In
this context, filter means to allow or block network traffic by processing it
through administrator-defined rules. By default, incoming traffic is blocked
unless it is a response to a request by the host (solicited traffic) or it is specifically
allowed (that is, a firewall rule has been created to allow the traffic). You
can configure Windows Firewall with Advanced Security to explicitly allow
traffic by specifying a port number, application name, service name, or other
criteria.
Windows
Firewall with Advanced Security also allows you to request or require that
computers authenticate each other before communicating, and to require the use
of data integrity or data encryption when communicating.
Managing Firewall Settings
The
Windows Firewall with Advanced Security is a host-based firewall that runs on
Windows Server 2012 and is turned on by default. Firewall settings within
Windows Server 2012 are managed from within the Windows Firewall MMC (Microsoft
Management Console). To review and set Firewall settings perform the following:
1.
Open the Server Manager
from the task bar.
2.
Click the Tools menu and
select Windows Firewall with Advanced Security.
3.
First review the current
configuration settings by selecting Windows Firewall Properties from the MMC
landing page. This allows access to modify the settings for each of the three
firewall profiles, Domain, Private, and Public as well as IPSec settings.
Applying Custom Rules – Inbound
Rules
Custom
Rules allow the finest level of control over inbound and outbound traffic to
your Windows Server 2012.
1.
If you have not done so
already load the Windows Firewall MMC by opening the Server Manager from the task
bar, clicking the Tools menu, and selecting Windows Firewall with Advanced
Security.
2.
Select either Inbound
Rules or Outbound Rules under Windows Firewall with Advanced Security on the
left side of the management console.
Note: This will provide a listing on each of the currently
configured firewall rules. Rules that are currently enabled are denoted by
green checkbox icon, while disabled rules display a grey checkbox icon.
Rightclicking a rule will allow you toggle enable/disable.
3.
From the right side of
either the Inbound Rules or Outbound Rules tab click New Rule.
4.
Select Custom from the
Rule Type radial button and click Next.
5.
Select the Program
association for the Custom Firewall Rule either All programs or the path to a
program and click Next.
6.
From the Protocol type
field select the protocol type and click Next.
Note: This
walkthrough uses TCP on port 80 (HTTP) for example purposes.
7.
Select an IP address
association for both local and remote addresses and click Next.
8.
Select an action to take
on matching traffic and click Next.
9.
Select the profiles
associated with the custom rule and click Next.
10.
Provide a name for your
Firewall rule and an optional description and click Finish.
11.
Once created the rule
will be enabled. The firewall rule can be found on the corresponding Rule tab,
either inbound or outbound depending on the type created. To disable or delete
the rule find the rule in the MMC, right-click it, and select either Disable
Rule or Delete.
12.
Open Server Manager,
click Add roles and features.
13.
On the Before you begin
window, click Next.
14.
On the Select
installation type, select Role-based or feature-based installation then click
Next.
15.
On the Select destination
server window, click Next.
16.
On the Select server
roles, select Web Server (IIS) then click Next.
17.
On the Select features
window, click Next.
18.
On the Web Server Role
(IIS) window, click Next.
19.
On the Select role
services window, click Next.
20.
On the Confirm
installation selections window, select “Restart the destination server
automatically if required”, click Install.
21.
On the Installation
progress window, click Close to finish.
22.
On Srv2012, run Internet
Explorer then type localhost and press enter.
23.
On Clt01 (client), run
Internet Explorer then type http://192.168.1.1 and press enter, Internet
Explorer cannot display the webpage.
24.
On Srv2012 server, on
Windows Firewall with Advanced Security window, click Inbound Rules, right
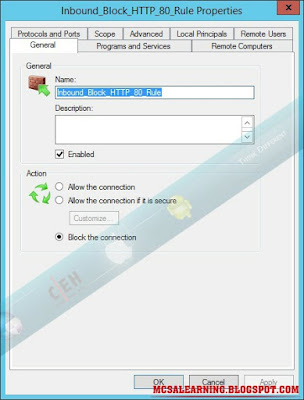
click Inbound_Block_HTTP_80_Rule and click Disable Rule.
25.
On Clt01 client, refresh
page and successful connection on HTTP port.
Applying Custom Rules – Outbound
Rule
1. On Srv2012 server, on the Windows Firewall with Advanced Security window, right click Outbound Rules then click New Rule.
2. On the Rule Type window, select Custom then click Next.
3. On the Program window, select All programs then click Next.
4. On the Protocol and Ports window, under Protocol type, select TCP from the drop-down menu. Under Remote port, select Specific Ports from the drop-down menu then type 80 and click Next.
5. On the Scope window, select These IP addresses in “Which remote IP addresses does this rule apply to?” then click Add.
6. On the IP Address window, select “This IP address or subnet” type 123.30.215.27 (dantri.com.vn’s IP) and click OK then click Next.
7. On the Action window, select Block the connection then click Next.
8. On the Profile window, click Next.
9. Provide a name for your Firewall rule and an optional description and click Finish.
10. Open Internet Explorer then type dantri.com.vn to address bar and press enter -> This page can’t be displayed.
11. On Srv2012 server, on Windows Firewall with Advanced Security window, click Outbound Rules, right click Outbound_Block_HTTP_80_DANTRI and click Disable Rule.
12. Open Internet Explorer then type dantri.com.vn to address bar and press enter, successfully connected to the address dantri.com.vn.
▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬
► Download this video, lesson for FREE
► MP4 link: updating...
► PDF link: http://adf.ly/1n3zoq
► Youtube: updating...
► Alternate link: http://fas.li/t9kLE
► Alternate link: http://viid.me/qWYHH1► Alternate link: http://linkshrink.net/7Q6FFn
▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬▬




































No comments:
Post a Comment